用搜索引擎搜索了一下域名,发现很多文章被一个站点给爬了,毫无保留:
这些年折腾的硬件

桌子上的两块显示器还是13年刚来青岛的时候买的显示器,已经伴随自己多年了。由于显示器一直使用没有什么问题,所以目前也没有换显示器的需求。等哪天有一个坏了,那就两个一块再换一个更大的。桌面上的两块安卓平板,一块是自己10年前买的第一代nexus 7,中间自己想换电池,结果把主板弄挂了,于是又买了一块主板,顺利的将16g的n7 升级成了32g的,虽然现在也没啥用了,目前,他的功能是一块钟表(运行的钟表app有点丑,谁有好看的可以给我推荐一下)另外一块是台电的平板,系统比较旧,但是可以长时间不息屏,于是现在用来链接控制智能家居的树莓派,用作远程显示器,桌子上的手机就无视掉吧。
KU138爬虫 【22.05.23】【Windows】

****************************************************************************************************
USAGE:
spider -h <help> -a <all> -q <search>
Arguments:
-a <download all site images>
-q <query the image with keywords>
-h <display help text, just this>
Option Arguments:
-p <image download path>
-r <random index category list>
-c <single category url>
-e <early stop, work in site crawl mode only>
-s <site url eg: https://www.v2ph.com (no last backslash "/")>
****************************************************************************************************
微图坊爬虫 【22.05.16】【Windows】

使用参数:
****************************************************************************************************
USAGE:
spider -h <help> -a <all> -q <search>
Arguments:
-a <download all site images>
-q <query the image with keywords>
-h <display help text, just this>
Option Arguments:
-p <image download path>
-r <random index category list>
-c <single category url>
-e <early stop, work in site crawl mode only>
-s <site url eg: https://www.v2ph.com (no last backslash "/")>
****************************************************************************************************
无法加载文件activate.ps1,因为在此系统上禁止运行脚本
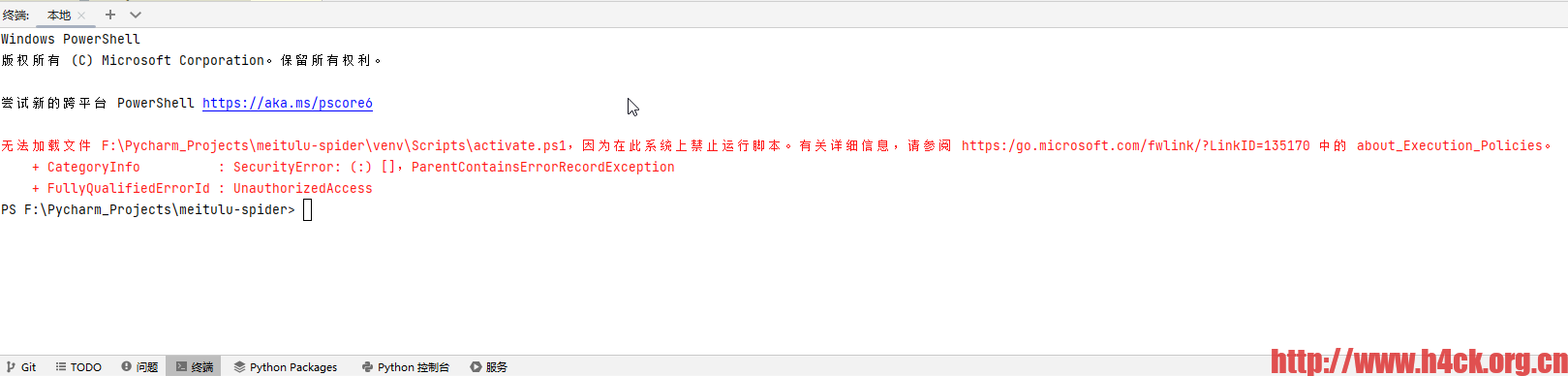
晚上想修改python的代码,结果打开pycharm直接报错了。
Windows PowerShell
版权所有 (C) Microsoft Corporation。保留所有权利。
尝试新的跨平台 PowerShell https://aka.ms/pscore6
无法加载文件 F:\Pycharm_Projects\meitulu-spider\venv\Scripts\activate.ps1,因为在此系统上禁止运行脚本。有关详细信息,请参阅 https:/go.microsoft.com/fwlink/?LinkID=135170 中的 about_Execution_Policies。
+ CategoryInfo : SecurityError: (:) [],ParentContainsErrorRecordException
+ FullyQualifiedErrorId : UnauthorizedAccess
PS F:\Pycharm_Projects\meitulu-spider>
局域网助手Lanhelper 1.99【纯水】
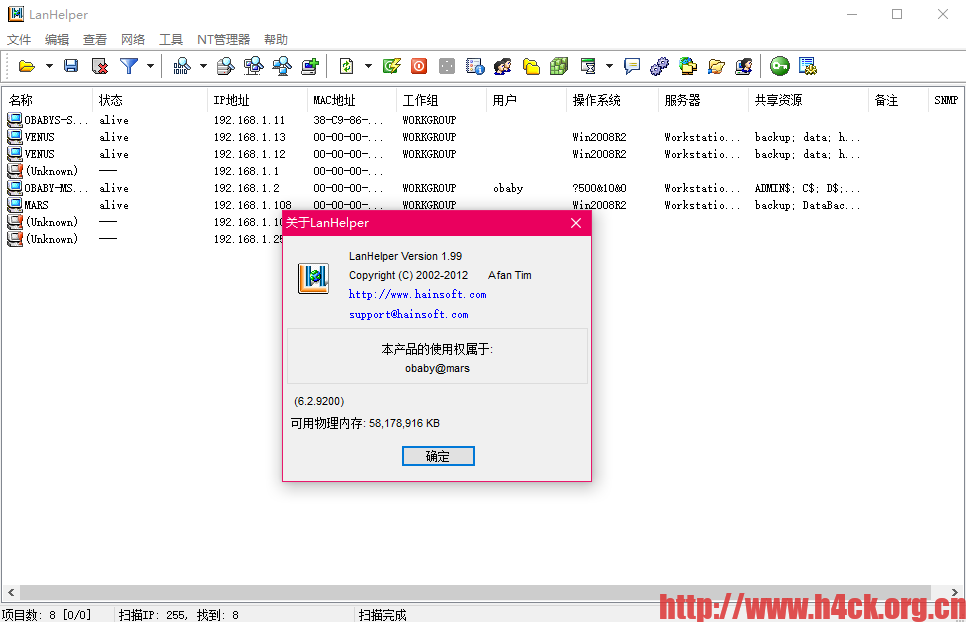
局域网助手 LanHelper 专门为高效高速的局域网管理而设计,是一个强大的网络管理、扫描、监控软件。提供有详细实时的日志给网络管理员有助于发现和解决问题。LanHelper集成有大量管理功能,同时不需要额外安装任何服务端软件。
LanHelper具有智能而快速的扫描引擎,IP扫描器和局域网扫描器能够扫描的信息包括IP地址、MAC地址、SNMP、NetBIOS、工作组名称、当前用户名称、操作系统类型、共享文件夹等。